Protect Your Journey
The user journey is not only an experience, but also a threat surface area for your business.
This is applicable to you, if you're:
An enterprise ecommerce company
An online marketplace
A consumer startup with online users
A neobank or fintech company
A brand with a digital presence
Teams Involved
Marketing team
Security team
Trust & Safety team
Legal & Compliance team
Account Creation
Promo abuse, synthetic identity fraud, and buyer-seller collusion are some of the biggest forms of abuse at account creation. The risk is centered around people creating false identities or abusing campaigns for new users. A strategy to address this form of fraud is the most nuanced, based on industry regulations and user risk.
Reward
- Maximize marketing dollars
- Unlock products and features only offered to trusted users
- Easily store information for future purchases, usage of product, user history
- Ability to provide special offers, promos, and discounts
Risk
- Waste promotional dollars recruiting the same user to your platform.
- Derailing engineering timelines
- Free trial and referral abuse
- Fake and synthetic identities
- Storing sensitive data and PII make you a target for data breaches
- Fake accounts
- Buyer-seller collusion
- Bringing on a disjointed list of case management tooling, making it hard to make decisions efficiently.
What to do?
- Confirm user identity using KYC (Know Your Customer) services.
- Verify users' identity documentation
- Utilize identity intelligence tools and exclude individuals with AML or OFAC concerns (based on identity information and related account history)
- Use data intelligence tools to score risks around emails, IP addresses, phone numbers, etc.
- Depending on trust & risk levels, change the in-product user experience with smart friction such as a request for more information or further risk checks
- Define policies for manual agent review
- Create a queue of risky users for agent review
- Develop a method to keep the team accountable
| Do it yourself | Dodgeball | |
|---|---|---|
| Integrate a KYC provider | 3 days | 15 minutes |
| Integrate an identity verification provider | 7 days | 15 minutes |
| Integrate an identity intelligence provider | 3 days | 15 minutes |
| Integrate a fraud engine or model to score risky behavior | 7 days | 15 minutes |
| Stitch together the above providers into a single view of a user with a decisioning framework | 1-3 months | 0 minutes |
| Create rule strategy for thresholds of risk | 3 days | 30 minutes |
| Create and implement rules | 1 day | 5 minutes |
| Add a centralized case management tool with queue and reporting | 3 days | 5 minutes |
| Learning, integrating, and testing add’l cutting-edge tools | 21 days | 15 minutes |
Try the Account Creation template in Dodgeball for free!
Chat with us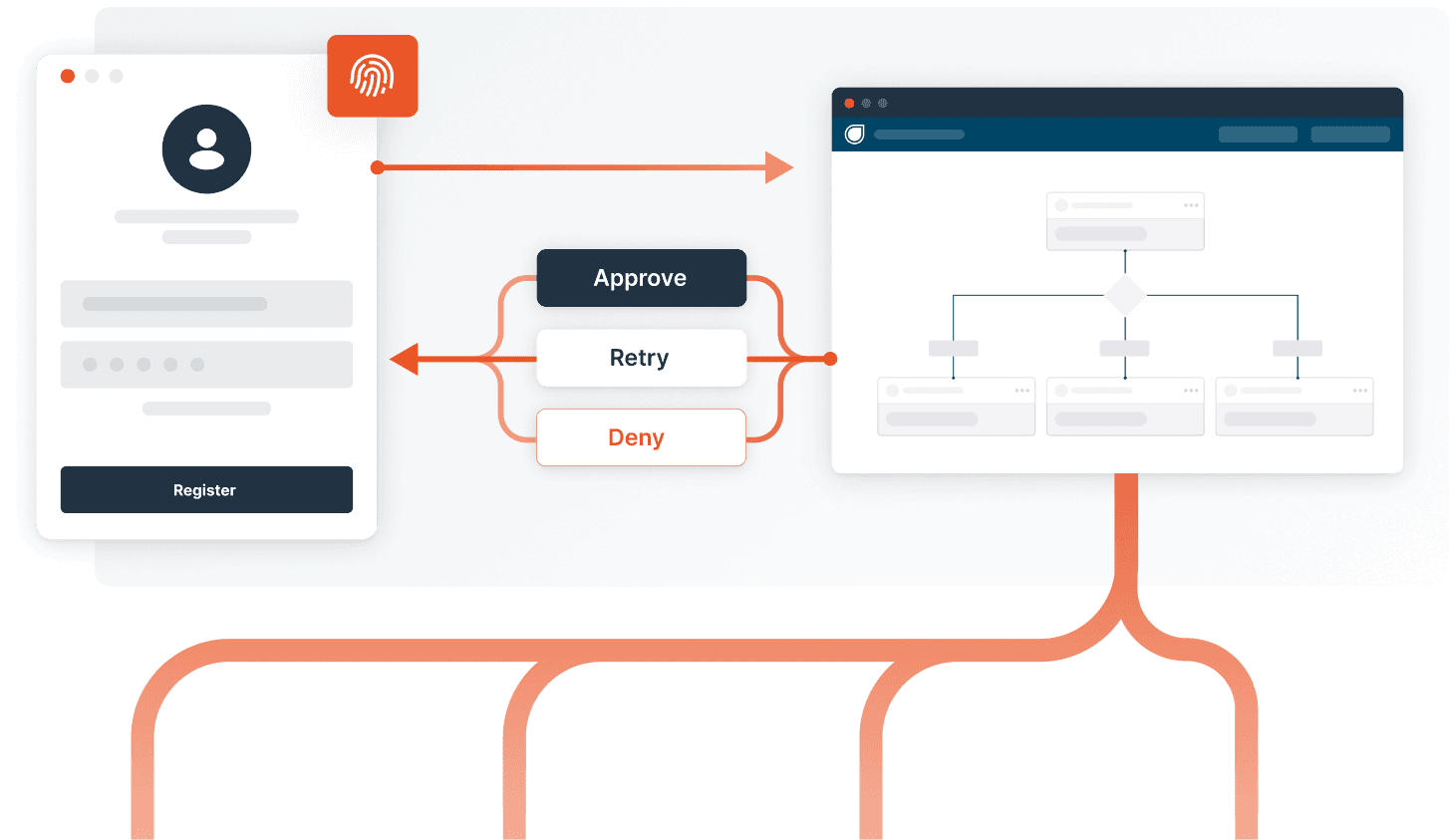
Teams Involved
Security team
Product team
Trust & Safety team
Login
Account Takeover is the biggest threat at this milestone. The risk revolves around your users being impersonated and their information or finances getting compromised.
Reward
- Let your customers return to the site
- Store information and payment to make recurring shopping easier
- Gain rewards and loyalty
- Make the experience feel customized
Risk
- Account Takeover and unauthorized access
- Phishing
- Too much friction turns away good customers
- Fraudsters gaining PII to support Identity Theft efforts
- Draining of funds or credits on account
- Making your customers feel unsafe
What to do?
- Cross-reference logging-in user details with existing user data to spot anomalous behavior (identity and behavior)
- Use a risk scoring tool to quantify matches and provide a nuanced experience
- Build an email alert for users when a suspicious sign-in is detected on their account
- Build a multi-factor authentication system for risky sign-ins
- Integrate a bot detection provider
- Check users’ referral urls with URL intelligence
- Link similar changes in user account details and flag these accounts for MFA or review
- Define policies for manual agent review
- Create a queue of suspect users for agent review
- Develop a method to track cases and keep the team accountable
| Do it yourself | Dodgeball | |
|---|---|---|
| Integrate frictionless KYC | 3 days | 15 minutes |
| Integrate a behavior and device intelligence provider | 3 days | 15 minutes |
| Integrate a fraud engine that supports login scoring | 7 days | 15 minutes |
| Stitch together the above providers into a single view of a user with a decisioning framework | 1-3 months | 0 minutes |
| Deploy multi-factor authentication | 14 days | 15 minutes |
| Integrate email intelligence | 3 days | 15 minutes |
| Create rule strategy for thresholds of risk | 3 days | 30 minutes |
| Create and implement rules | 1 day | 5 minutes |
| Add a centralized case management tool with queue and reporting | 3 days | 5 minutes |
| Learning, integrating, and testing add’l cutting-edge tools | 21 days | 15 minutes |
Try the Account Takeover template in Dodgeball for free!
Chat with us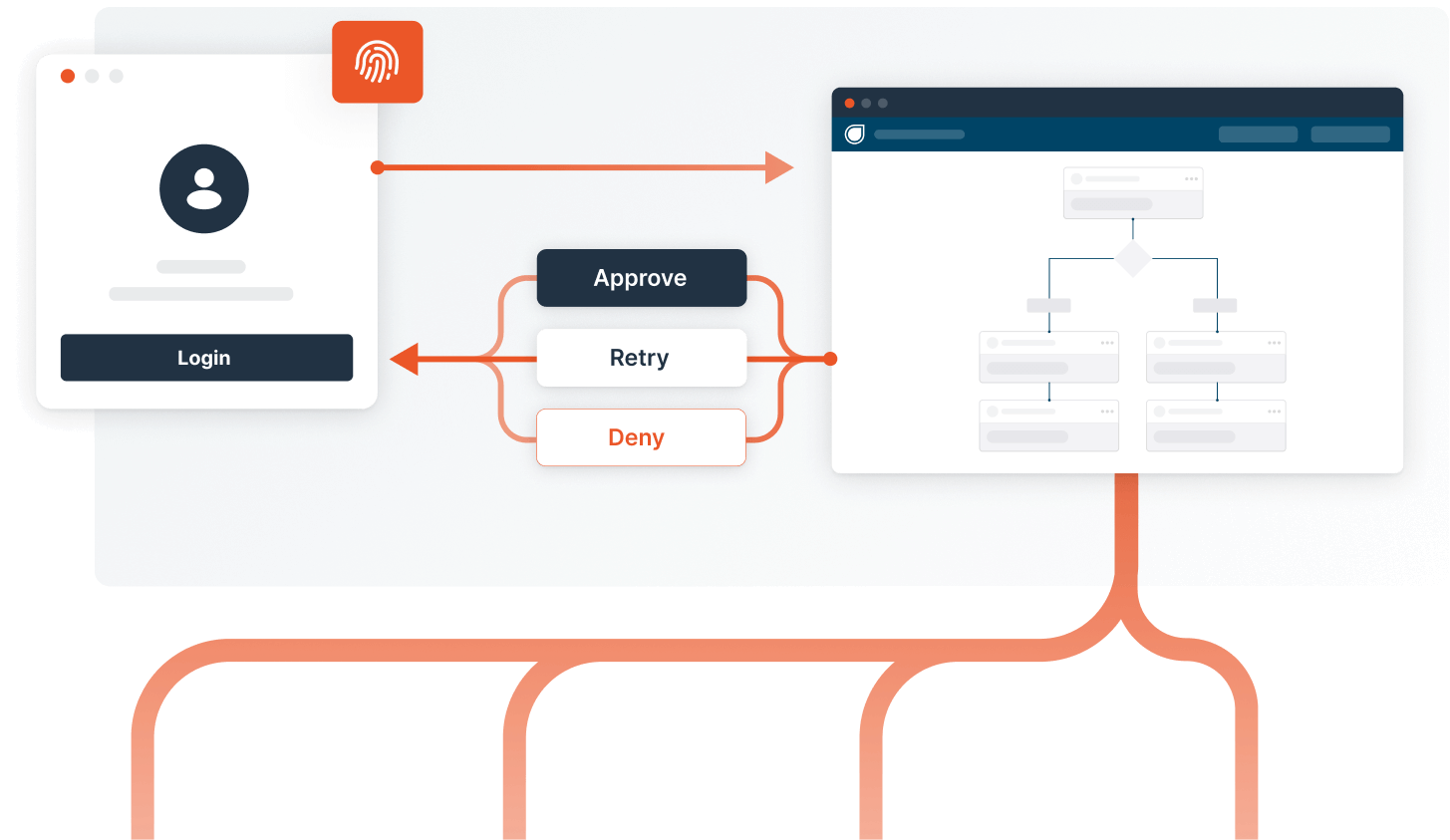
Teams Involved
Payments team
Finance team
Trust & Safety team
Product & Engineering team
Customer Support team
Checkout
Payment fraud is the biggest threat at checkout. The risk revolves around fraudulent users using legitimate cardholder’s payment methods or legitimate users misusing their own cards by creating false chargebacks.
Reward
- Collect payments
- Cater to global audience
- Accept different types of payments to increase conversions
Risk
- Chargebacks and associated fees
- Increased fraud
- Card testing to check whether stolen card information is valid
- Too much fraud leads to monitoring programs with card issuers
- High risk merchants can be shut off by banks or even issuers
- Refund abuse and "friendly" fraud
- Too much user friction
- Reputational risk to a bad experience
What to do?
- Validate user and confirm user identity using KYC (Know your customer) services
- Utilize behavior and intelligence data to spot fraudulent users
- Use a fraud engine to score transactions and provide alternate experiences based on the resulting risk assessment
- Link together fraud signals using an orchestration service
- Deploy multi-factor authentication at login to prevent exploitation of vaulted cards
- Create rules for CVV (card verification value) or AVS (address verification service) requirements in your PSP (Payment Service Provider)
- Define policies for manual agent review
- Create a queue of suspect users for agent review
- Develop a method to track cases and keep the team accountable
| Do it yourself | Dodgeball | |
|---|---|---|
| Setup payment processor | 7 days | 7 days |
| Integrate frictionless KYC | 3 days | 15 minutes |
| Integrate a behavior and device intelligence provider | 3 days | 15 minutes |
| Integrate a payments fraud engine to score risky behavior | 7 days | 15 minutes |
| Stitch together the above providers into a single view of a user with a decisioning framework | 1-3 months | 0 minutes |
| Deploy multi-factor authentication | 14 days | 15 minutes |
| Implement CVV and AVS Requirements | 2 days | 15 minutes |
| Create rule strategy for thresholds of risk | 3 days | 30 minutes |
| Create and implement rules | 1 day | 5 minutes |
| Add a centralized case management tool with queue and reporting | 3 days | 5 minutes |
| Learning, integrating, and testing add'l cutting-edge tools | 21 days | 15 minutes |
Try the Payments template in Dodgeball for free!
Chat with us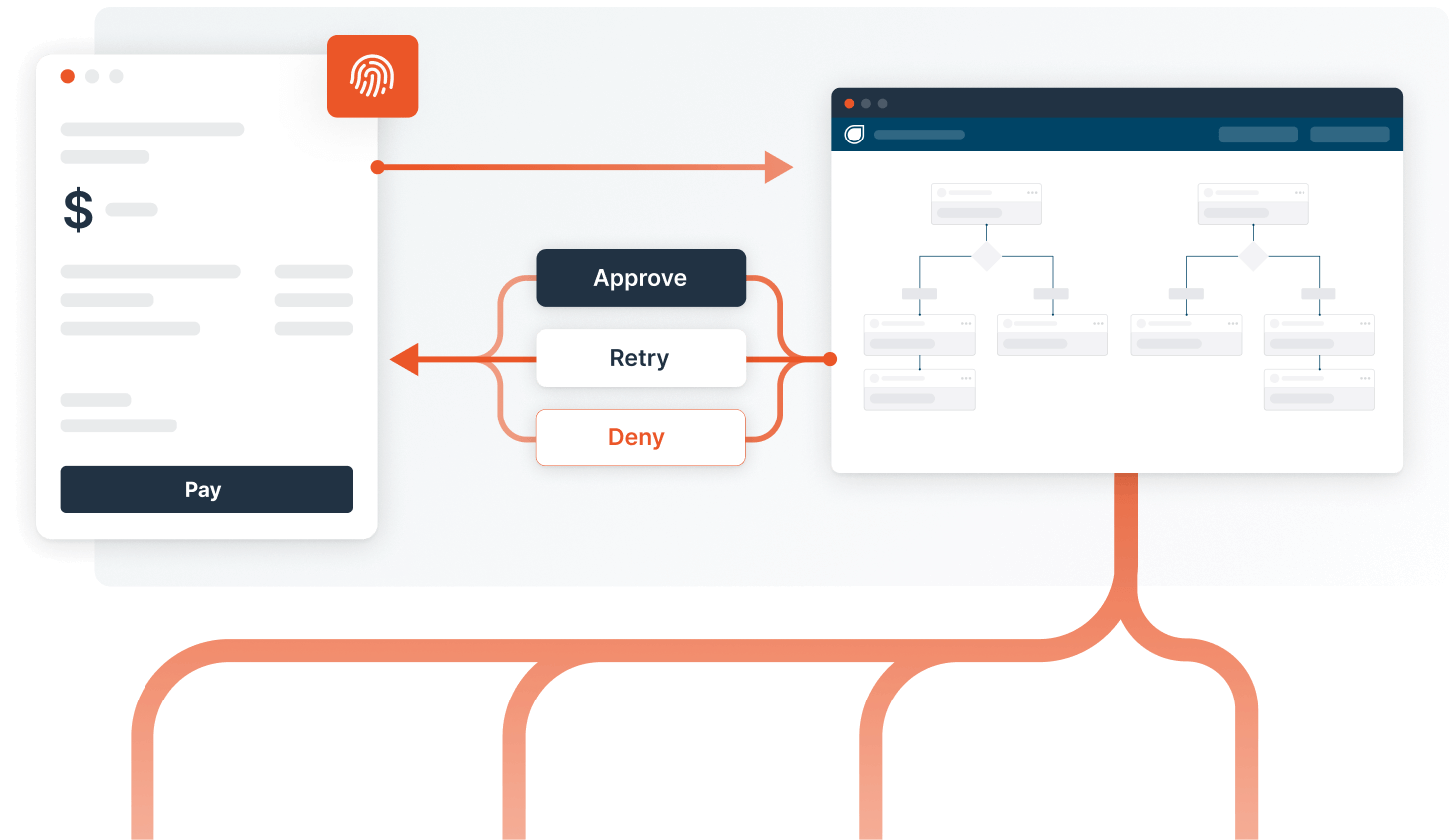
Teams Involved
Payments team
Finance team
Trust & Safety team
Product & Engineering team
Customer Support team
Chargeback
First-party fraud or chargebacks is the biggest threat to revenue post-checkout. The risk revolves around seemingly legitimate users creating false chargebacks. If you allow too many chargebacks, then payment providers will take a larger percentage in fees.
Reward
- Save on transaction costs
- Happier customers
- Save on manual investigation costs
- Enhanced revenue reporting
- Avoid non-refundable chargeback fees
- Reinvest recovered revenue back into the business
- All dispute data, including alerts, managed from a single dashboard
- Automatically submitted alert resolutions
Risk
- Chargebacks and associated fees
- Increased fraud
- Too much fraud leads to monitoring programs with issuers
- High risk merchants can be shut off by banks or even issuers
- Refund abuse and "friendly" fraud
- Too much user friction
- Reputational risk to a bad experience
What to do?
- Setup chargeback deflection and chargeback recovery tools
- Connect to payment processor, fraud prevention tools, and customer platform
- Develop process for monitoring and disputing alerts and chargeback notifications as they are received
- Create Compelling Evidence Templates
- Build logic to automatically create and submit responses on your behalf as chargebacks come in
- Define chargeback management strategy and policies including manual agent review
- Create a queue of specific chargeback incident for agent review
- Develop a method to track cases and keep the team accountable
| Do it yourself | Dodgeball | |
|---|---|---|
| Integrate Ethoca Alerts | 7 days | 15 minutes |
| Integrate Verifi Alerts & RDR | 7 days | 15 minutes |
| Integrate Chargeback Automation | 7 days | 15 minutes |
| Centralize Alerts/Disputes with Transaction and User data | 14 days | 5 minutes |
| Review Alerts and Chargeback Notifications | 30 minutes | 0 minutes |
| Investigate and Determine Response | 15 minutes | 0 minutes |
| Collect Transaction and User Specific Data | 5 minutes | 0 minutes |
| Create Compelling Evidence including compiled data | 30 minutes | 0 minutes |
| Create Chargeback Management Strategy | 3 days | 15 minutes |
| Create and implement rules | 1 day | 5 minutes |
| Add a centralized case management tool with queue and reporting | 3 days | 5 minutes |
| Learning, integrating, and testing add'l cutting-edge tools | 21 days | 15 minutes |
Try the Chargebacks template in Dodgeball for free!
Chat with us